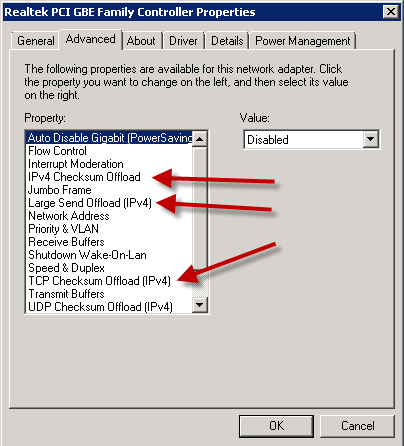
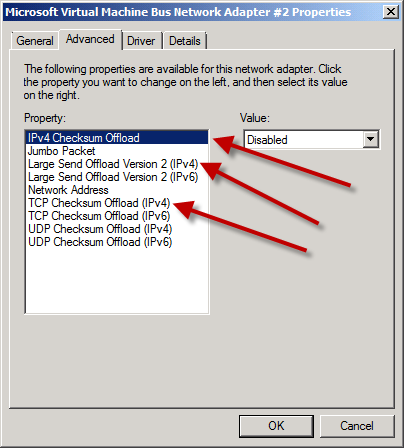
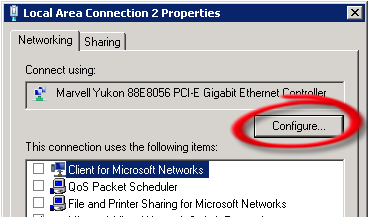
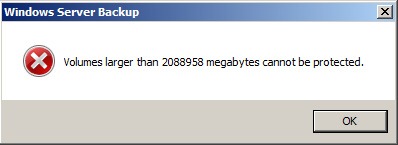
Here is a list of cultures from the Microsoft Silverlight supported cultures listing (CultureInfo Class) that I have discovered are not currently (11/11/2010) NOT supported on the Windows Phone 7 platform.
|
ar-DZ |
Arabic (Algeria) |
|
ar-BH |
Arabic (Bahrain) |
|
ar-EG |
Arabic (Egypt) |
|
ar-IQ |
Arabic (Iraq) |
|
ar-JO |
Arabic (Jordan) |
|
ar-KW |
Arabic (Kuwait) |
|
ar-LB |
Arabic (Lebanon) |
|
ar-LY |
Arabic (Libya) |
|
ar-MA |
Arabic (Morocco) |
|
ar-OM |
Arabic (Oman) |
|
ar-QA |
Arabic (Qatar) |
|
ar-SA |
Arabic (Saudi Arabia) |
|
ar-SY |
Arabic (Syria) |
|
ar-TN |
Arabic (Tunisia) |
|
ar-AE |
Arabic (U.A.E.) |
|
ar-YE |
Arabic (Yemen) |
|
hy-AM |
Armenian (Armenia) |
|
zh-HK |
Chinese (Hong Kong SAR, PRC) |
|
zh-MO |
Chinese (Macao SAR) |
|
zh-SG |
Chinese (Singapore) |
|
hr-BA |
Croatian (Bosnia and Herzegovina) |
|
dv-MV |
Divehi (Maldives) |
|
fa-IR |
Farsi (Iran) |
|
gu-IN |
Gujarati (India) |
|
he-IL |
Hebrew (Israel) |
|
hi-IN |
Hindi (India) |
|
kn-IN |
Kannada (India) |
|
kk-KZ |
Kazakh (Kazakhstan) |
|
syr-SY |
Syriac (Syria) |
|
ta-IN |
Tamil (India) |
|
te-IN |
Telugu (India) |
|
th-TH |
Thai (Thailand) |
|
ur-PK |
Urdu (Pakistan) |
|
vi-VN |
Vietnamese (Vietnam) |