You may have discovered that deleting an Azure Active Directory is a particularly frustrating experience that ultimately ends in failure. The new portal have improved things a bit, by running through a series of check before the delete button is enabled.
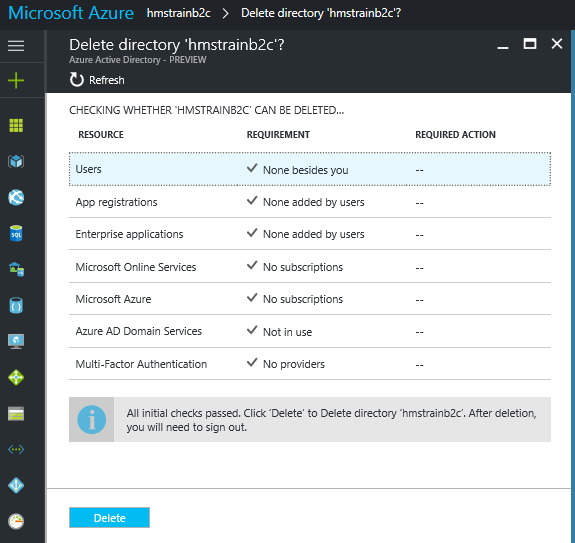
You may need to go back to the Classic portal (https://manage.windowsazure.com) to see some of the objects/resources to delete.
However, although this will help you remove ‘most’ of what you need to, unfortunately NOT all!
In this case I got a “Unable to delete directory”
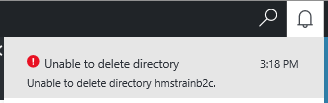
Clicking through on this Alert you may get something like “Tenant has enabled service principals“!
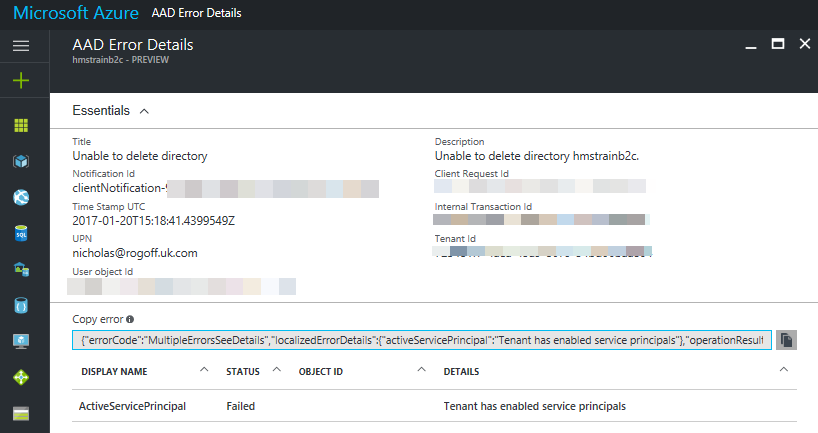
In the new portal, these should appear in the ‘Enterprise Applications’ …I think, but that didn’t happen for me. However, in the classic portal I did see two ‘Applications’ remaining (Office 365 Management APIs & Visual Studio Online), despite having never specified this myself. How they got there is another discussion. In my case, this was just a quick test of creating a B2C Active Directory, that had no additional actions taken other than creation.
B2C Applications
If you have created a B2C Active Directory and you are not able to delete the AD because it says there is a still a registered application, then you may need to remove the application from that blade in the portal first.
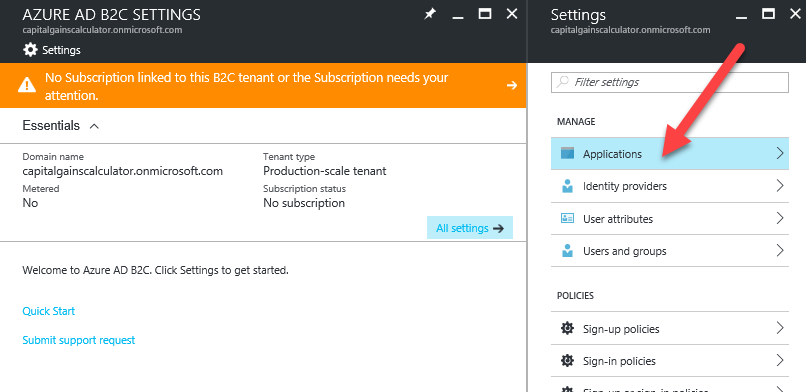
You may also need to do this if you try to remove any Registered Applications in PowerShell using something like (see Step 3 below)
Get-AzureADApplication | Remove-AzureADApplicationand you get the ‘Deletion of multi-tenant application is currently not supported.‘ error as below.
Remove-AzureADApplication : Error occurred while executing RemoveApplication StatusCode: BadRequest ErrorCode: Request_BadRequest Message: Deletion of multi-tenant application is currently not supported. At line:1 char:26 + Get-AzureADApplication | Remove-AzureADApplication + ~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : NotSpecified: (:) [Remove-AzureADApplication], ApiException + FullyQualifiedErrorId : Microsoft.Open.AzureAD16.Client.ApiException,Microsoft.Open.AzureAD16.PowerShell.RemoveApplication
Walk-through of deleting the AAD Tenant
The first step is to ensure you have a ‘local’ Global Admin account in this tenant that you can leave as the only account. As this AD Tenant did not exist when you created it, you would have probably used either an Office 365 or Microsoft account to create it.
Step 1 – Add a ‘local’ Global Admin User
So, you need to Add a User. The easiest way is to use the Classic portal as this includes a more helpful dialog.
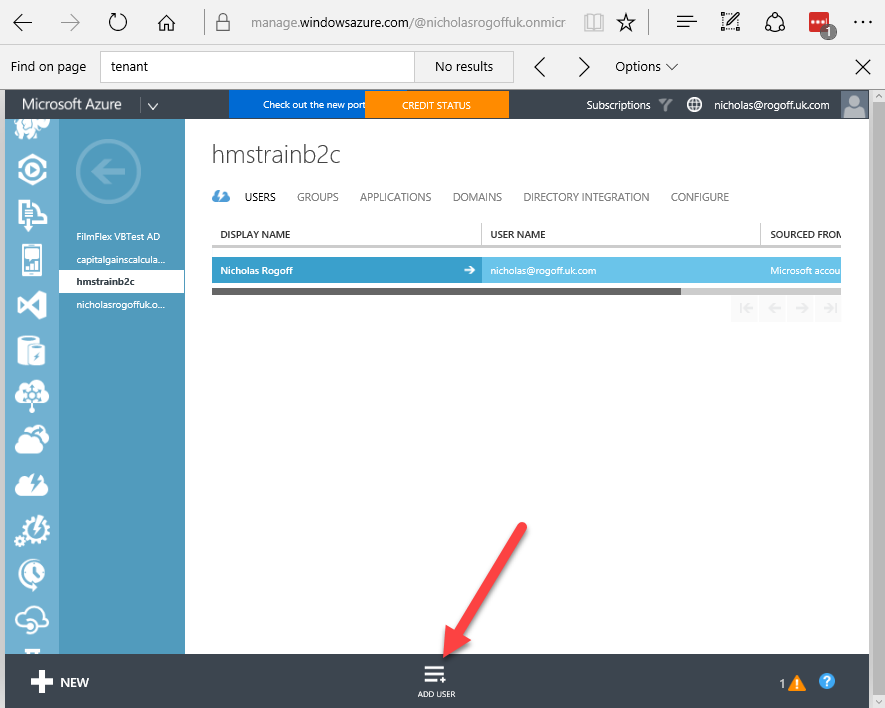
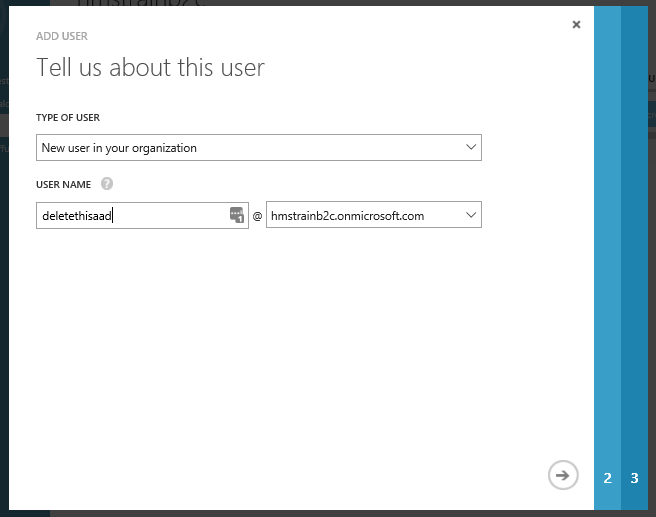
Make a note of the ‘onmicrosoft.com‘ username. Here I have called it deletethisaad@hmstrainb2c.onmicrosoft.com
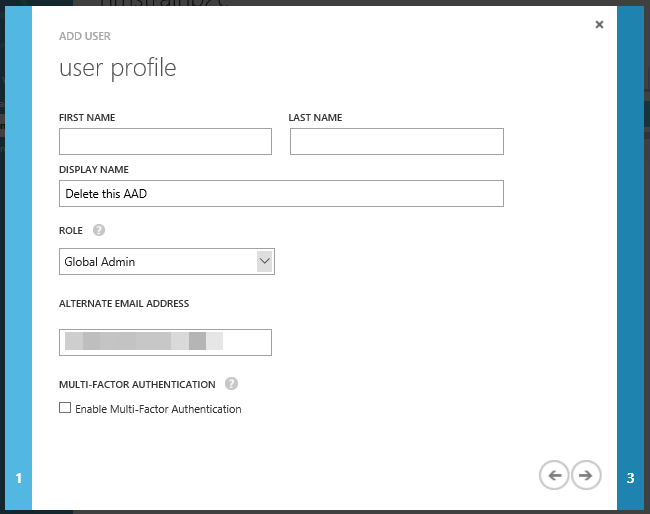
Make sure you select ‘Global Admin‘ and enter an ‘Alternative Email Address’.
Then click ‘Create‘ and make a copy of the new password.
Step 2 – Login and change the password of the new ‘local’ user
You will now need to login as this new user and you will be forced to change the password. Best to use an ‘Incognito’/’InPrivate’ browser tab for this.
In your new ‘InPrivate’ tab go to https://portal.azure.com

Step 3 – Use PowerShell to remove all Principals
Unfortunately (if you don’t like coding!) you will need to use PowerShell to remove the Service Principals mentioned in the AAD Error Details.
Firstly make sure you have the AzureAD PowerShell module installed (this is the newer V2 cmdlets) . To do this I suggest using the ‘Windows PowerShell ISE‘ (make sure it’s NOT the ‘Windows PowerShell ISE (x86)’ if you’re on a 64-bit OS. This is because when you install the module it will be the one appropriate to your OS and things may fail). You will also need to run it as a local administrator using the ‘Run as administrator‘ (right-click on the shortcut) to successfully install the module.
To install the AzureAD Powershell module run the following
# Need to ensure install the module, Need to 'Run as administrator'
Install-Module AzureADOnce installed, now run the following PowerShell commands (personally I would run them one by one just to be sure and check the responses). You will be prompted to enter the new password for the new account you just created.
# Log in to the AD Tenant with your new 'Local' account
$username ="{replace this with your new username}"
$adcred = Get-Credential -UserName $username -Message "Enter the password"
Connect-AzureAD -Credential $adcred
#Confirm you have the correct Tenant
Get-AzureADTenantDetail | select DisplayName
#Get Service Principles
Get-AzureADServicePrincipal | select DisplayNameYou may see a list like
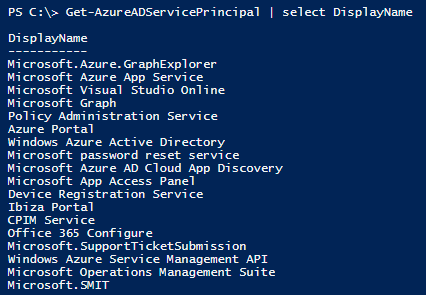
# Delete the Principals
Get-AzureADServicePrincipal | Remove-AzureADServicePrincipal
# Check if any Service Principles are left
# Leave these if any as they may be mandatory!
Get-AzureADServicePrincipal | select DisplayNameYou can do the same process for any registered applications too. Just substitute ‘ServicePrincipal‘ with ‘Application‘.
Step 4 – Remove the original User account
You can either do this from the portal or using PowerShell. Just make sure you get the right User account (not the one you have just created)! If using the portal you will need to login with the new account.
# List all user accounts
Get-AzureADUser
# Now make sure you can just select the original one.
# Copy the display name from the previous command and use as a search string
Get-AzureADUser -SearchString "{replace with search term. e.g. DisplayName}"
#Get and delete a user
Get-AzureADUser -SearchString "{replace with search term. e.g. DisplayName}" | Remove-AzureADUser
#Check that you are left with just the new account
Get-AzureADUserStep 5 – Delete the Azure Active Directory Tenant
Log into the portal (https://portal.azure.com) using the new account.
Go to Azure Active Directory > Overview and click Delete, as you probably did before!
Hopefully it will finally be gone without error! Do comment if you have any different experiences.
🙂
Azure
Attribution
I do owe a big thanks to Eric Golp whose blog entry I based this updated walk-through on. You can find the original at https://blogs.msdn.microsoft.com/ericgolpe/2015/04/30/walkthrough-of-deleting-an-azure-ad-tenant/
One thought on “How to delete an Azure Active Directory (ADD) Tenant”